Dec 22, 2007
Nov 21, 2007
Mozilla Launching Firefox 3.0 Beta 1

Mozilla Corp. Monday nov,19 has released the first beta of Firefox 3.0, but continued to warn most users to stick with production Version 2.0.
"We do not recommend that anyone other than developers and testers download the Firefox 3 Beta 1 milestone release, It is intended for testing purposes only." Mike Beltzner, Mozilla's interface designer, said in a note posted to the company's development center.
But while the official word was for users to stand clear, Beltzner's personal recommendation was a lot less intimidating. "It's a preview release, so use with caution and don't expect your add-ons to work without some magic; but between you and me, I've been running on this 'developer preview' for at least three months, and have never looked back," he said in a post to his own blog.
Beltzner also touted several of the improvements in Firefox 3.0, including new security features and tools, a redesign of the bookmarking and browser history and numerous back-end platform enhancements, but he said they all require more testing and user feedback. The company has posted a more complete list of new features in the release notes it added to its Web site Monday.
On the security side, Firefox 3.0 adds malware check, a phishing filter-like feature that warns users attempting to reach a URL blacklisted for suspected malicious code hosting; one-click site information that displays site ownership; fixes for vulnerabilities in plug-in updating; and integration with antivirus software and Windows Vista's parental control settings.
Mozilla also claimed that it has fixed more than 300 individual memory leaks and added a new cycle collector to eliminate other memory issues. Firefox has a reputation for leaking memory -- consuming large quantities the longer it's left running, and ultimate slowing down its host computer -- although some of its developers have contested the claims, and even pegged the problem as one of perception.
Most current Firefox plug-ins -- Mozilla calls them extensions -- will not work with Firefox 3.0, a stumbling block for some who might otherwise want to test the preview. "Users of the latest released version of Firefox should not expect their add-ons to work properly with this beta," the beta's release notes read.
Firefox 3.0 Beta 1 can be downloaded for Windows, Mac OS X and Linux in 21 language versions from Mozilla's site.
Nov 2, 2007
Novell BorderManager Client Trust Buffer Overflow Vulnerability
The vulnerability is caused due to the Client Trust application incorrectly processing validation requests sent to the UDP port on which clntrust.exe is listening (by default 3024). This can be exploited to cause a heap-based buffer overflow by sending a specially crafted validation request containing a Novell tree name without backslash or zero wide characters.
Successful exploitation allows execution of arbitrary code.
The vulnerability is reported in Novell BorderManager 3.8. Prior versions may also be affected.
Solution : Download patch from Vendor
(http://download.novell.com/Download?buildid=AuOWp2Xsvmc~)
6 Related Secunia Security Advisories
1. Novell BorderManager Unicode Encoding Detection Bypass2. Novell BorderManager ISAKMP Predictable Cookie Security Issue
3. Novell BorderManager VPN Denial of Service Vulnerability
4. Novell BorderManager Proxy Potential Denial of Service
5. Novell Bordermanager VPN Service Unspecified Denial of Service
6. Novell BorderManager 3.7 SP2 fixes multiple issues
Other Release at 2007-11-01 from Secunia.com
Read more after jumpSep 28, 2007
New tools help hack into iPhone
By Robert McMillan
New tools help hack into iPhone
HD Moore, one of the developers of the Metasploit hacking software, is supporting the iPhone within the Metasploit framework and providing tools to run 'shellcode' promptsiPhone hackers have some new tools now, thanks to HD Moore, one of the developers of the Metasploit hacking software.
On Tuesday, Moore announced that he was supporting the iPhone within his Metasploit framework and released software that would allow hackers to run "shellcode" command prompts on Apple's mobile device.
By integrating the iPhone into Metasploit, it will now be a little easier for hackers to gain access to someone else's iPhone, but they will also need a few other tools to succeed. First, they will need to create working exploit code, which takes advantage of bugs in Apple's software, to trick the device into running the shellcode. They will also need to create more sophisticated "payload" applications that can do things like remotely connect with the hacker. "It's a first step," Moore said of his hack.
With iPhone prices dropping and noticeable improvements in the quality of iPhone hacking tools, Apple's phone has become a more interesting target of late, Moore said.
And the iPhone has obviously hit a nerve in the security community. Moore said that about a quarter of the attendees at the recent Black Hat conference in Las Vegas had the devices. "It's trendy," he said. "It kind of creeped me out when I saw how many people had iPhones when I went to Vegas."
In fact, hackers have already developed a number of exploits that they claim could be used on the iPhone's Safari browser.
And security researchers have even demonstrated how the iPhone can be compromised. In July, a Baltimore, Maryland, company called Independent Security Evaluators showed how it could run unauthorized software on an iPhone by taking advantage of a Safari bug.
Moore believes that the iPhone's browser and mail client will be the best sources of bugs and he said that because of the components and information stored on the phone, it may end up being a more attractive target than the PC.
For example, the phone could be used to track someone's location based on information from cell phone towers. Throw in the iPhone's microphone, camera, and an Internet connection, and you suddenly have a device that could be used to secretly keep tabs on people, Moore said. "If you look at what you get by exploiting someone's iPhone, you actually get a lot more than you do from someone's PC a lot of the time," he said.
Sabotaging Google
John C. Dvorak - PC Magazine
A reader, Courtney Cox (no relation to the actress), recently pointed out to me that the top results of recent complex Google searches turned out to be inane Chinese sites that were not even parking sites, just an assortment of keywords that somehow got indexed and brought to the top of the results list. After seeing a few of these sites, I have to wonder what's going on. Is it sabotage?Let's start by showing you a typical site: http://vmk.wtoxd.cn/xmijotb.html (there's some annoying Active X here. So visit at your own risk). This site was the top result listed when the search term "reset mp3 player m240d" was entered. And here are the full search results , in which nine of the top ten results are these weird Chinese sites.
Courtney sent me numerous examples of this phenomenon, and it's obvious that the more specific and detailed the search request, the more likely Google is to list these Chinese sites. The issue has apparently been reported to Google, but if the basic algorithms allow this sort of result, even banning the specific sites will not stop this sort of abuse.
Right now the motives behind this phenomenon are obscure, unless it's being done just for testing purposes. You know, like underground nuclear testing.
I'm reminded of some news reports I read in The New York Times as I was doing some Civil War–era research in old copies of the paper circa 1860 to 1870. At that time, the telegraph was the hot technology, and it was being built out all over the country using telegraph poles and wires strung everywhere. During this era it was not uncommon for one of the telegraph companies to chop down the poles and cut the wires of another telegraph company. There were constant news stories about it, and this sort of thing still exists. It's no different than a phone company "accidentally" unhooking a competitor's DSL rig in the central office during the burst of open-access activity in the 1990s.
I remember my first visit to China 20 years ago, listening to the long lectures about how China intends to become a capitalist nation. The Chinese liked to say they were going to emulate American capitalism. Ever since then I wondered what that meant. Would it mean chopping down telegraph poles? The American way? —next: Gaming the System
When I see this sort of site at the very top of a list of Google results, I wonder how hard it would be to scuttle Google by gaming the system. I don't think Yahoo! or even Microsoft has thought of this. But if not, why not? Perhaps one of the two companies is indeed behind the Chinese sites. Who would know?
We do already know that Google is susceptible to Google-bombing and click fraud. Now we have this. We also know that Google's search results include far too many parking sites. So many, in fact, that there are brokers who will turn all your domains into parking sites for a revenue split. You've all seen these parking sites. Many are done as typo sites: Mistype a URL and you wind up at some site that is nothing more than links to various shopping and search sites that generally have nothing to do with anything. In some instances, these sites appear on the first page of Google search results. As far as I'm concerned, they should not appear at all. And while they're an eye-rolling nuisance to readers of PC Magazine, you can be certain that multitudes of rubes using the Internet think that they're real sites.
As Google gets bigger and more dominant, you can be certain that the competition will come up with some way to ruin Google and make it simply unusable. I have to assume that these Chinese sites, which serve no purpose other than to scramble Google, are a step in that direction.
On that note, I should add that entering "reset mp3 player m240d" on Yahoo! yielded worse returns, with all the results being weird Chinese sites—including one that tried to load a Trojan (caution!!) that AVG killed immediately. When the same search terms were used on MSN, there were no results at all.
Sep 21, 2007
Vista Infected By Virus Stoned.Angelina
New Info
A batch of laptops pre-installed with Windows Vista Home Premium was found to have been infected with a 13-year-old boot sector virus.Those of you with a long memory will vividly recall the year 1994: Nirvana's lead singer Kurt Cobain died, South Africa held its first multi-racial elections, and Tony Blair became leader of the Labour party. Oh, and Microsoft's operating system was the quaint, pre-NT Windows for Workgroups.
Click here to find out more!
But it was a year that also saw the arrival of a boot sector computer virus known as Stoned.Angelina which moved the original master boot record to cylinder 0, head 0, sector 9.
It would appear that this teenage virus has not yet been consigned to the history books.
According to Virus Bulletin , the consignment of infected Medion laptops – which could number anything up to 100,000 shipments – had been sold in Danish and German branches of retail giant Aldi.
The computers had been loaded with Microsoft's latest operating system Vista and Bullguard's anti-virus software, which failed to detect and remove the malware.
Although the infection itself is harmless, Stoned.Angelina will undoubtedly have left Microsoft and Bullguard execs blushing with embarrassment about the apparent flaws in their software which allowed an ancient virus to slip through the back door.
On its website Bullguard offered some reassurance to Medion customers hit by the virus:
"Stoned.Angelina is a low-risk boot virus that infects the MBR (Master Boot Record) of hard disks. This is a very old virus. Apart from its ability to spread from computer to computer, it carries no payload (damage) to the systems it infects."
It added that the virus commonly spreads by being booted from an infected floppy disk, and causes no damage to the operating system.
Virus Bulletin technical consultant John Hawes said: "This is a reminder that old viruses never really die.
"Malware that's been off the radar for years often pops up when least expected, after someone digs out an old floppy or boots up an ancient system, and security firms have a duty to maintain protection against older threats for just this kind of eventuality."
Original source
Sep 8, 2007
Novell Client For Windows Vista
 Novell Netware now support Windows Vista , you can download Vista Client here or Click on image
Novell Netware now support Windows Vista , you can download Vista Client here or Click on imageSystem requirements
The Novell Client for Windows Vista is supported on the following platforms:* Windows Vista Business (x86 or x64)The Novell Client for Windows Vista might run but is not supported on Windows Vista Starter, Windows Vista Home Basic, and Windows Vista Home Premium editions. This Client will not run on Windows XP, 2000, or 2003.
* Windows Vista Enterprise (x86 or x64)
* Windows Vista Ultimate (x86 or x64)
Key features
* Support for Novell Open Enterprise Server (OES) 1, OES 2, NetWare 5.1/6.0/6.5
* File system integration with NSS and non-NSS volumes via NCP
* Login script processing
* Notification area (Red N) options
* Integrated login with Windows Vista (single username and password)
* NMAS™ client integration
* Forgotten password recovery options
* LDAP contextless login support
* DFS junctions
* Support for 802.1x wireless authentication
* DHCP options
* OpenSLP support
* Shell extensions for Windows Vista�s file browser
* File caching/shared open mode support
* Auto-reconnect
* Cluster failover support
* Property pages, NCIMAN, and updating Client settings
Sep 7, 2007
Apple iTunes Music File Buffer Overflow Vulnerability
 According to Secunia.com , a vulnerability has been reported in Apple iTunes, which can be exploited by malicious people to compromise a user's system.
According to Secunia.com , a vulnerability has been reported in Apple iTunes, which can be exploited by malicious people to compromise a user's system.The vulnerability is caused due to an unspecified boundary error when processing album cover art. This can be exploited to cause a buffer overflow via a specially crafted music file.
Successful exploitation may allow execution of arbitrary code.
The vulnerability is reported in versions prior to 7.4.
Solution : Update your iTunes Software to version 7.4.
iTunes 7.4 for Mac:
http://www.apple.com/support/downloads/itunes74formac.html
iTunes 7.4 for Windows:
http://www.apple.com/support/downloads/itunes74forwindows.html
Related Article :
1. Apple iTunes Music File Buffer Overflow Vulnerability2. Apple QuickTime Multiple Vulnerabilities
3. Apple QuickTime Java Extension Two Vulnerabilities
4. Apple QuickTime Java Extension "toQTPointer()" Code Execution
5. Apple QuickTime Multiple Vulnerabilities
6. Apple Quicktime RTSP URL Handling Buffer Overflow Vulnerability
7. Apple QuickTime Plug-In Local Resource Linking Weakness
8. Apple QuickTime Multiple Vulnerabilities
9. Apple iTunes AAC File Parsing Integer Overflow Vulnerability
10. QuickTime Multiple Code Execution Vulnerabilities
Aug 25, 2007
Hacks let the iPhone roam
"I'm sorry about how hard they are to follow, but someone will get them to work, and simplify them, and simplify them more," he said of the ten steps his method requires to unlock the phone. "Hopefully a software unlock will be found in the near future."
Unknown to Hotz, that's exactly what has happened. A group calling itself IPhoneSimFree has claimed to have unlocked the iPhone just via software -- a claim that has been verified by mobile-device news site Engadget. By unlocking the phone, the group claims that any provider can be used in any country.
Video - Strom Site
The Zhelatin/Storm Gang has been very busy lately. Their spamming tactics have changed from sending an attachment to sending a link that directs recipients to an IP Address. The HTML used by their sites is variable, and also differs depending on the browser.
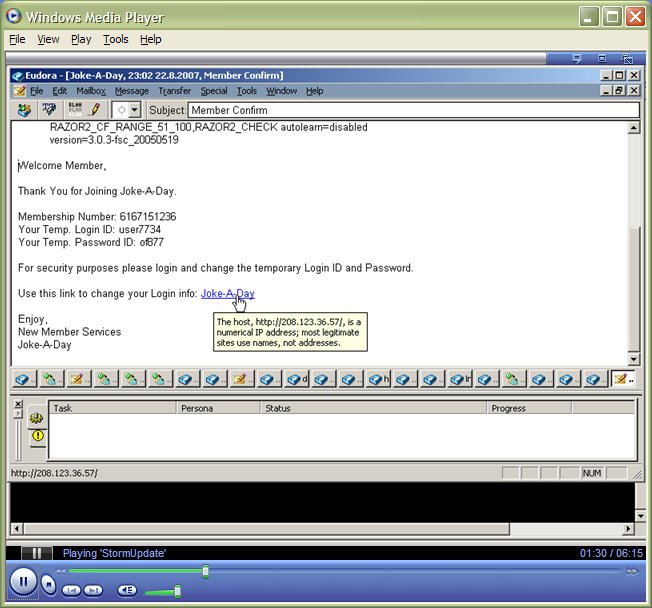
The video is available via F-secure YouTube Channel.
Aug 10, 2007
Microsoft Windows Vista Performance Update 1.0
Microsoft Windows Vista Performance Update will improve the performance of Windows Vista in certain scenarios. Additional information about this update can be found in KB Article 938979.
Latest Changes:
* You experience a long delay when you try to exit the Photos screen saver
* A memory leak occurs when you use the Windows Energy screen saver
* If User Account Control is disabled on the computer, you cannot install a network printer successfully. This problem occurs if the network printer is hosted by a Windows XP-based or a Windows Server 2003-based computer
* When you write data to an AVI file by using the AVIStreamWrite function, the file header of the AVI file is corrupted
* When you copy or move a large file, the "estimated time remaining" takes a long time to be calculated and displayed
* After you resume the computer from hibernation, it takes a long time to display the logon screen
* When you synchronize an offline file to a server, the offline file is corrupted
* If you edit an image file that uses the RAW image format, data loss occurs in the image file. This problem occurs if the RAW image is from any of the following digital SLR camera models: Canon EOS 1D & Canon EOS 1DS
* After you resume the computer from hibernation, the computer loses its default gateway address
* Poor memory management performance occurs
Aug 7, 2007
Tips to Unlock iPhone
 Sassha (senior member at Hackintosh forums from Croatia) claims have successfully managed to "unlock" the iPhone by using a variety of detailed steps to trick the iPhone into using a non-AT&T SIM card.
Sassha (senior member at Hackintosh forums from Croatia) claims have successfully managed to "unlock" the iPhone by using a variety of detailed steps to trick the iPhone into using a non-AT&T SIM card.You will need :
1. iPhone
2. SIM Reader/Writer
3. SilverCard
4. V1 SIM card
5. Download - http://simemu.gsmhosting.net/SIM_EMU_6.01_CFG_v2.1.zip
6. Download - http://www.kinforce.com/down/kinforc...rsim/ws109.zip
For detail tips you can read here
Aug 4, 2007
Apple says iTunes sales top 3 billion songs !
 Apple company, which makes the market-leading iPod digital media player, said iTunes has sold more than 3 billion songs since its launching four years ago, media reported Wednesday.
Apple company, which makes the market-leading iPod digital media player, said iTunes has sold more than 3 billion songs since its launching four years ago, media reported Wednesday.The milestone came just six months after iTunes, Apple Inc.'s online music download service, surpassed the 2 billion tracks-sold mark. The service was launched in April 2003 and, until February 2006, sold its first 1 billion songs.
ITunes has surpassed Amazon.com Inc. and Target Corp. to become the third-largest music retailer in the United States, according to media reports.
The iTunes catalog contains over 5 million songs, 550 television shows and 500 movies.
Apple's line of iPod portable music players has been key to iTunes' popularity.
In April, Apple company said it had sold more than 100 million iPods. It reached that milestone in the five and a half years since the first iPod was sold.
Perhaps most importantly, Apple offered not just the downloading service but also the hardware for managing music collections.
"They've made it brain-dead simple to buy, download and move content around onto iPods, computers and now iPhones," said Gartner analyst Mike McGuire.
Analysts refers to this as the digital music "ecosystem," which comprises the hardware, software and downloading service. Each plays a role in giving Apple a leading share of the digital music world.
Source:Xinhua/people.com
Aug 3, 2007
Microsoft Windows URI Handling Command Execution Vulnerability
The vulnerability is caused due to an input validation error within the handling of system default URIs with registered URI handlers (e.g. "mailto", "news", "nntp", "snews", "telnet"). This can be exploited to execute arbitrary commands when a user e.g. using Firefox visits a malicious website with a specially crafted "mailto" URI containing a "%" character and ends in a certain extension (e.g. ".bat", ".cmd")
Examples:
mailto:test%../../../../windows/system32/calc.exe".cmdSuccessful exploitation requires that Internet Explorer 7 is installed on the system.
nntp:../../../../../Windows/system32/telnet.exe" "secunia.com 80%.bat
The vulnerability is confirmed on a fully patched Windows XP SP2 and Windows Server 2003 SP2 system using Firefox version 2.0.0.5 and Netscape Navigator version 9.0b2. Other versions and browsers may also be affected.
Solution:
Do not browse untrusted websites or follow untrusted links.
BETA test the new Secunia Personal Software Inspector!
 The Secunia PSI detects installed software on your computer and categorises it as either Insecure, End-of-Life, or Up-To-Date. Effectively enabling you to focus your attention on software installations where more secure versions are available from the vendors.
The Secunia PSI detects installed software on your computer and categorises it as either Insecure, End-of-Life, or Up-To-Date. Effectively enabling you to focus your attention on software installations where more secure versions are available from the vendors.Highlights of The Secunia PSI:
* The Secunia PSI will be available free of charge
* Calculates your unique Secunia System Score
* Automatically scans your computer
* Enables you to update Insecure/End-of-Life software
* Provides Direct Download Links to security updates & patches
* Detects and advises on more than 4,200 applications
* Direct correlation between thousands of Secunia Advisories and your specific system and software
* Secure SSL encrypted connection to Secunia
How does the Secunia PSI work
The Secunia PSI works by examining files on your computer (primarily .exe, .dll, and .ocx files). These files contain non-specific meta information provided by the software vendor only. This data is the same for all users, and originates from the installed programs on your computer - never from their configuration. Please read the privacy statement available at the bottom of this page and through the Secunia PSI application for more details about how information from your computer is used by Secunia.
After examining all the files on your local hard drive(s), the collected data is sent to Secunia's servers, which match the data against the Secunia File Signatures engine (https://psi.secunia.com/) to determine the exact applications installed on your system.
This information can then be used to provide you with a detailed report of the missing security related updates for your system.
System Requirements:
The current list of requirements that must be met for the Secunia PSI to function correctly are the following:
Supported Operating Systems:
* Microsoft Windows XP - Service Pack 2
* Microsoft Windows 2003
* Microsoft Windows 2000 - Service Pack 4
* US and European languages only
* Learn more
Jul 27, 2007
iPhone, Apple PCs vulnerable to hackers: consultant
 The iPhone and Apple Inc.'s desktop computers may be vulnerable to hackers due to a flaw in their Web browser, according to a security firm, which said it found a way to hack into the iPhone.
The iPhone and Apple Inc.'s desktop computers may be vulnerable to hackers due to a flaw in their Web browser, according to a security firm, which said it found a way to hack into the iPhone.Baltimore-based Independent Security Evaluators, which tests its clients' computer security by hacking it, said on Monday that three employees found a way to take control of iPhones through a Wi-Fi link or by tricking users into going to a Web site.
Charles Miller, principal security analyst at the firm, said a security weakness allows someone to take control of Apple's Safari Web browser and see other applications on the device at the same time, which could potentially make users of Macintosh desktop computers vulnerable to attacks.
"The same problem actually exists on Apple's desktops," said Miller. But he added that while his firm had identified the risk for both desktops and phones, it had written only the code necessary to hack into the iPhone.
The security consultants, who took about a week and a half to work out the move, said they were able to take control of an iPhone and make calls or send text messages, as well as access e-mails, voice-mail, address books and call and Web browsing history.
Miller said his company gave details about the hack and a potential security patch to Apple, but did not publicly release the details.
"We're looking into the report submitted by (Integrated Security Evaluators) and we always welcome feedback on how to improve our security," Apple spokeswoman Lynn Fox said.
Miller said Apple could have avoided the risk by eliminating links between the browser and other applications.
"It turns out that on the iPhone there are probably some basic things they could have done that would have made it better," said Miller.
The claim comes more than three weeks after Apple and AT&T Inc. (T.N: Quote, Profile, Research) started selling Apple's first cell phone, which includes a music and video player as well as a Web browser.
As many as 700,000 iPhones were sold on the first weekend after the June 29 launch, according to analyst estimates.
Days after launch, a well-known hacker Jon Johansen, claimed to have overcome restrictions on the iPhone, allowing highly technical users to bypass AT&T's network to use the phone's Internet and music features.
While cell phones have not historically been as vulnerable to attack as desktop computers, some experts worry that phones take on greater risks as they add more computer-like features.
Miller said he had not looked into security on other mobile phones to see how they compare to the iPhone, but said the more complex a system is, the greater the likelihood is that it will have problems.
source: reuters.com
Jul 26, 2007
New Sophos Security Threat Report Reveals Record Number of Web-Borne Attacks During 2007
Sophos, a world leader in IT security and control, has published new research on the first six months of cybercrime in 2007. The Sophos Security Threat Report examines existing and emerging security trends and has identified a sharp increase in the number of web threats, as well as the countries and server types hosting the most infected sites.
The first half of 2007 has seen a significant increase in threats spread via the web, which has surpassed email as the preferred method of attack for financially motivated cybercriminals. In June alone, Sophos’s global network of monitoring stations uncovered a record number of infected web pages - approximately 29,700 - each day. In contrast, earlier in 2007, only as few as 5,000 malicious pages per day were detected.
Sophos blocks access to millions of web pages to protect customers from malware and inappropriate content. Taking a snapshot of just one million of those web pages, experts found that 28.8 percent were hosting malware. An additional 28 percent were blocked due to the adult nature of their content, most commonly because they were pornography or gambling sites. Pages created by spammers accounted for 19.4 percent and 4.3 percent were classed as illegal sites, including phishing sites or those peddling pirated software. Of the websites containing malicious code, just one in five had been designed specifically for malicious activity, with the remaining 80 percent made up of legitimate sites that have fallen victim to hackers.
APACHE IS THE MOST COMPROMISED SERVER
By compromising a single file on a web server, cybercriminals can easily and quickly cross-contaminate a huge number of websites, as the infected file may form part of a plethora of unrelated pages, all of which are published from the same server.
The breakdown of the world’s top server types affected by web threats in the first six months of 2007 reads as follows:
1. Apache 51.0%
2. Microsoft IIS 6 34.0%
3. Microsoft IIS 5 9.0%
5. nginx 3.0%
Other 3.0%
The fact that more than half of all infected web pages were hosted on Apache servers demonstrates that infection is not simply a Windows problem. Earlier this year, during a global ObfJS attack, in which legitimate sites were compromised so that they could serve up a malicious code, 98 percent of affected servers were running Apache - many of which were hosted on UNIX rather than Windows platforms.
“Website infections have increased significantly in the past six months. The number of infected sites has grown more than five times since January,” said Ron O’Brien, Boston-based Sophos senior security analyst. “As 80 percent of those sites are legitimate, it makes you wonder why more action is not taken to help prevent such attacks. Simple measures such as keeping up to date with security patches are one of the most effective ways to prevent infections on servers.”
TOP WEB-BASED THREATS OF 2007 - SO FAR
The top 10 list of web-based malware hosted on these infected sites during the first six months of 2007 reads as follows:
1. Mal/Iframe 49.2%
2. Troj/Fujif 7.9%
3. JS/EncIFra 7.3%
4. Troj/Psyme 8.3%
5. Troj/Decdec 6.9%
6. Troj/Ifradv 4.1%
7. Mal/ObfJS 2.5%
8. Mal/Packer 1.5%
9. VBS/Redlof 1.1%
10. Mal/FunDF 0.9%
Other 10.3%
Mal/Iframe, which works by injecting malicious code onto web pages, dominates this chart, accounting for almost half of the world’s infected URLs. Furthermore, it shows no sign of abating - in a recent potent attack, more than 10,000 web pages were infected, the majority of which were on legitimate web pages hosted by one of Italy’s largest ISPs.
MOST INFECTED WEB PAGES HOSTED IN CHINA
The top 10 list of countries hosting malware-infected web pages during the first half of 2007 reads as follows:
1. China 53.9%
2. United States 27.2%
3. Russia 4.5%
4. Germany 3.5%
5. Ukraine 1.2%
6. France 1.1%
7. Canada 0.8%
8. United Kingdom 0.7%
9= Taiwan 0.6%
9= South Korea 0.6%
Other 5.9%
China, which at the end of 2006 hosted just over a third of all malware, has now overtaken the U.S., and in the first six months of 2007 was responsible for hosting more than half of all web threats reported to Sophos. China’s dramatic rise in the chart is primarily due to widespread Mal/Iframe infections on Chinese hosted web pages. In fact, more than 80 percent of the country’s compromised web pages are infected with this malware.
HACKERS TURN TO PDFS AND REMOVABLE DRIVES TO COMMIT CYBERCRIMES
The first half of 2007 has seen cybercriminals using attachments in spam messages. To avoid detection by less sophisticated gateway filtering products, there is a growing trend for spammers to use PDF files carrying a graphical version of their marketing message, in their attempt to reach potential customers.
Hackers have also taken advantage of users who have “auto-run” enabled on their Windows PC to automatically execute malicious code as soon as an infected removable flash drive is attached to the computer. Notable examples this year were the LiarVB-A worm, which spread information about AIDS and HIV via USB keys, and the Hairy worm, which claimed that teen wizard Harry Potter was dead. However, neither threat became widespread and both could be protected against by using up-to-date anti-virus software at the desktop.
”Using attachments to spread malware has decreased in the last few years, however, because PDF attachments are so trusted, they will remain high on the list for spammers looking for the file type most likely to be opened,” said O’Brien.
EMAIL STILL A CAUSE FOR CONCERN
Email threats continue to cause concern for businesses and, although they have become eclipsed by web-based threats, the actual amount of email-borne malware has remained constant during the past year. The proportion of infected email during the first half of 2007 was 1 in 337, or 0.29 percent of all messages. More than 8,000 new versions of the Mal/HckPk threat were seen during 2007, as it was used to disguise widespread email attacks like Dref and Dorf.
More information about the latest trends in malware, spyware and spam can be found in the complete version of the latest Sophos Security Threat Report, which can be downloaded from: http://www.sophos.com/securityreport
A journalist-specific edition is available from: http://www.sophos.com/securityreportjul2007
McAfee set to launch Rootkit Detective application
This new product has been designed to detect and remove dangerous rootkit attacks. The company claims that this application would help end-users ward off the threats. It would also be used to provide the company information relevant information to company’s ongoing research operations.
This application would complement their existing offering SiteAdvisor which warns the users about potentially unsafe websites on the web. McAfee said that Rootkit Detective will be offered at no charge from its Web site via download.
Rootkit Detective has been designed to find hidden kernel processes and registry entries. They would be removed when the system is restarted the next time.
It would also be able to test the integrity of a PC’s kernel memory and track any modifications that might also highlight rootkit activity. They have already provided a beta version of the application which is being tested by thousands of users worldwide.
Joe Telafici, vice president of operations at McAfee Avert Labs added in a statement on this new product: “Dealing with rootkits will always be an arms race; the whole process is a game of challenge-and-response between the hackers and security community, and as the authors have advanced the complexity of their attacks, we need to continually update our own technologies to keep up. We started putting rootkit detectors into our products in 2006, and this is the next stage in advancing our detection technologies.”

Secunia Personal Software Inspector now available for BETA Testing
“The free Secunia Personal Software Inspector is the next evolution of the Secunia Software Inspector series”, says Thomas Kristensen, CTO of Secunia. “Like the Software Inspector and the Network Software Inspector, it is designed to inspect what software you have on your computer, whether you have the latest version and security patches, and if not, how you can upgrade to the latest safe version”.
“We really felt that there was a need to make the average user aware of the dangers of leaving your applications unpatched”, says Kristensen. Most Windows users are aware of Microsoft Patch Tuesday, he adds, because it is heavily marketed and it notifies you in a userfriendly way that you need to take action.
However, Patch Tuesday only covers Microsoft products and not the very large number of equally dangerous vulnerabilities discovered in other software. Most people aren’t aware of these issues, or don’t want to spent hours every month hunting for the relevant information about security updates.
“Our idea to solve this is to make all this information available through a userfriendly interface to make it as easy as possible for people to check the security patch status of their software”, Kristensen adds.
Secunia is offering the PSI as a free tool for private individuals as part of our effort to make browsing the Internet a safer activity.
Users are invited to take part in BETA testing the Secunia Personal Software Inspector. The BETA version can be downloaded from: https://psi.secunia.com/
Both the BETA and final versions of the PSI are free. The final version will also be available from the Secunia website.
“We really want to highlight the emerging issues of private consumers not being aware of the possibility that their sensitive data can be exposed through their personal computer when applications are left unpatched”, says Kristensen. Patching applications, Kristensen adds, ensures that you are protected against currentlyknown software vulnerabilities and attack vectors from online criminals.
However, with the dozens of programs you have on your computer, trying to keep up with each upgrade is practically impossible. To do so would require you to spend a lot of time checking vendor websites and surfing the Internet for news on software vulnerabilities, and this just isn’t very feasible.
The PSI does all that for you, and more. With a click of the mouse, the PSI identifies the installed software on your computer, and determines which ones are secure, and which ones aren’t. It then tells you where you can download updates to turn your nonsecure software to secure software, making the transition from vulnerable computer to secured system as easy as 123. And did we mention it’s free?
To ensure that your computer is thoroughly inspected for vulnerable software, you just need to follow these three simple steps: Step 1 is to download the PSI from https://psi.secunia.com and run it on your personal computer. Step 2 is to check the inspection results for applications marked as “Insecure” and “Endoflife” (meaning they are no longer supported by the vendor). Step 3 is to check the vulnerability information to see where you can download the secure software version.
The PSI detects more than 4,200 different applications and versions, ensuring that whatever software you have installed in your system is monitored by Secunia for software flaws, security patches, and updated versions.
The final version of the PSI will also be though the Secunia websites, thirdparty download sites, and globally present partners. Our partners, who also share our concern regarding the rising level of unpatched applications, will be capable of distributing an easytouse tool compared to their current alternative of advising their users/customers to manually keep all applications patched.
Securityoriented organisations that cater to consumer needs, such as ISPs and banks, can also take advantage of the PSI to better inform their subscribers and account holders about the necessity of online security.
To detect what software you have on your network, Secunia uses its File Signature technology, which is composed of carefully programmed rules used to identify installed applications, and their exact versions on Windowsbased systems.
To detect if your software version is the latest nonvulnerable version available from the vendor, the Software Inspector uses Secunia Advisory Intelligence technology, which Secunia has been providing to the global IT community for over four years.
Secunia’s commercial services include vulnerability advisories and analysis, exploit code, binary analysis, and file signatures. The complete Secunia File Signature database contains more than 110,000 rules for detecting more than 4,200 unique applications and their exact versions.
To know more about the services that Secunia can provide for you and your company, please go to http://corporate.secunia.com.
Press Contact Information:
Thomas Kristensen, CTO
pr@secunia.com
Phone: +45 7020 5144
Fax: +45 7020 5145
New launching software - µTorrent mUI
The software has been designed to be light on the system and has become one of the most popular torrent client on the Windows platform.
The developers of this excellent software sometime back unveiled the first public beta of µTorrent’s WebUI.
This application enables the user to control the µTorrent application running on a machine through the web interface from anywhere in the world as long as they have access to the internet.
The latest news is that a mobile based version of this web interface to control the µTorrent application is scheduled to release today.
This new project has been named µTorrent mUI and it would be released in a beta version. They developers claim that the interface would work with any mobile with an internet web browser.
Next Windows OS (Windows 7) to ship within the next 3 years
However, market sources have now said that the company is likely to unveil their next OS release within the next three years.
It took the company around seven years to launch the Vista OS as they struggled with delays in the development process.
The next Windows OS is being called Windows 7 internally and it is likely to ship in consumer and business versions, and in 32-bit and 64-bit versions.
Microsoft is also considering launching a subscription based model for this next edition though not many details are available.
However, the next major software release from the company is expected to be the Service Pack 1 of Windows Vista OS.
Firefox 2.0.0.5 release fixes bug with Internet Explorer
The bug could have caused malicious code to run if the browser is launched by Microsoft’s Internet Explorer.
Both Microsoft and Mozilla claimed that the problem lied with the software from the other party.
Mozilla has now taken the initiative by releasing the fix which now patches the bug.
Mozilla added in a statement that the update would be delivered automatically to the users who have not disabled this specific option.
The developers added that this latest release also fixes seven other vulnerabilities. At least two of these are considered “critical” by Mozilla
Checkout: Firefox 2.0.0.5
Jul 25, 2007
Norton AntiVirus Virus Definitions July 24, 2007
Norton AntiVirus Virus Definitions description
Norton AntiVirus Virus Definitions contains the latest free virus databases for Norton AntiVirus Virus (NAV).Signature file updates ensure that your PC is protected from the latest viruses. It is very important to make sure that you have the latest signature on your PC.
As new threats emerge, Symantec immediately builds new Virus Definitions Updates and makes them available for download.
Supports the following versions of Symantec antivirus software:
· Norton AntiVirus 2003 Professional Edition
· Norton AntiVirus 2003 for Windows 98/Me/2000/XP Home/XP Pro
· Norton AntiVirus 2004 Professional Edition
· Norton AntiVirus 2004 for Windows 98/Me/2000/XP Home/XP Pro
·
Norton AntiVirus 2005 for Windows 98/Me/2000/XP Home/XP Pro
· Norton AntiVirus 2006 for Windows 2000/XP Home/XP Pro
· Norton AntiVirus 2007 for Windows XP Home/XP Pro/Vista
· Norton AntiVirus for Microsoft Exchange (Intel)
· Norton SystemWorks (all versions)
· Norton Utilities for Windows 95/98 (all versions)
· Symantec AntiVirus 3.0 for CacheFlow Security Gateway
· Symantec AntiVirus 3.0 for Inktomi Traffic Edge
· Symantec AntiVirus 3.0 for NetApp Filer/NetCache
· Symantec AntiVirus 8.0 Corporate Edition Client
· Symantec AntiVirus 8.1 Corporate Edition Client
· Symantec AntiVirus 9.0 Corporate Edition Client
· Symantec AntiVirus 10.0 Corporate Edition Client
· Symantec AntiVirus 10.1 Corporate Edition Client
· Symantec Mail Security for Domino v 4.0
· Symantec Mail Security for Domino v 5.0
Note: The i32 Intelligent Updater package cannot be used to update Symantec AntiVirus Corporate Edition 8.0 servers or Norton AntiVirus Corporate Edition 7.6 servers, but can be used to update Corporate Edition clients. The x86 Intelligent Updater package can be used to update Corporate Edition clients and servers.
Download from sofpedia - 17MB
Jul 20, 2007
Flash Player and Java Runtime Environment New Patch
Many of the vulnerabilities are cross-platform, and between them, they have most OS-browser combinations covered. You are vulnerable until you install the patches. Read the advisories from the vendors and grab the patches here and here.
There are no reported in-the-wild exploits yet, but we might see some soon as enough technical information required to build an exploit has been released publicly for at least a few of these vulnerabilities.
On 13/07/07 At 09:59 PM
Source : f-secure.com
Microsoft Patch July Edition
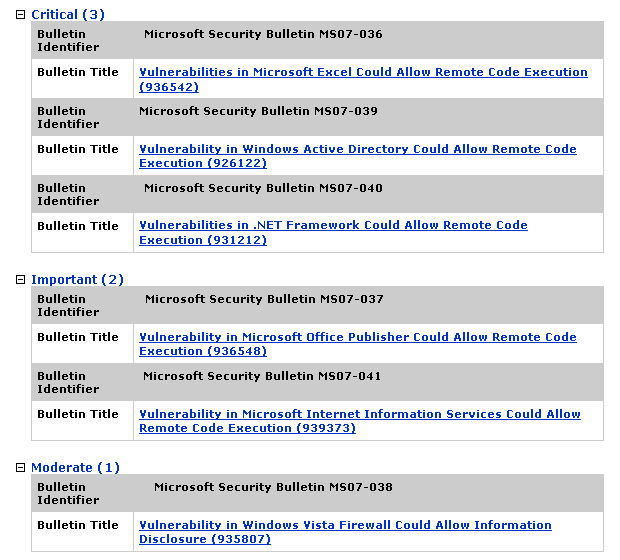
These updates cover vulnerabilities for several applications, including Office Excel, Windows Active Directory, and .NET Framework for the critical updates. Most of these vulnerabilities allow remote code execution and one allows information disclosure.
For more information as well as links for the actual patches, see July's bulletin.
FBI tracked 'teen bomber' using spyware
Fifteen year-old student Josh Glazebrook had the surveillance software sent to him by government agents after he threatened Timberline High School near Seattle.
According to an affidavit obtained by Wired News, FBI agent Norman Sanders described the software as a "computer and internet protocol address verifier".
The spyware program, which is known as CIPAV, logs the following:
"We have not seen any evidence that this practice is becoming commonplace, but there have been occasions when the crime-fighting authorities have used malware to their advantage," Cluley told vnunet.com.
- The computer's IP address
- The MAC address
- The person's username
- The last URL visited
- A list of open ports
- Computer programs that are running
- The operating system
- The internet browser and version
- The computer's registered owner
- The IP address of every other computer to which the PC connects for up to 60 days
"Way back in 2001 we wrote of our concerns about the FBI running a project called Magic Lantern which was designed to do just this."
Cluley explained that people supporting the use of spyware to monitor possible criminal behaviour often compared it to tapping a suspect's phone line.
"However, there is a difference between tapping a phone line and installing malicious code on a user's computer," he said.
"Malicious code on a user's computer can be copied, archived, adapted and potentially used by people who do not work for the authorities to spy on completely innocent victims."
Glazebrook pleaded guilty to felony harassment, making bomb threats and identity theft earlier this week.
Source
Jul 19, 2007
How Good Are You at Recognizing Fake Websites and Spam Emails ?
 Can you tell a fake (phishing) web site from a real one ? Or can you recognize spam emails that request you to verify your eBay or Paypal account credentials.
Can you tell a fake (phishing) web site from a real one ? Or can you recognize spam emails that request you to verify your eBay or Paypal account credentials.McAfee has created a very simple quiz with screenshots of websites and emails for you to spot the fake ones from the real site. Do take this 10 question quiz and the results may actually surprise you even when you are a pro-geek - it looks deceptively easy but that's not the reality.
My result only 3 question that i wrong, how about you ? simple test and helpfull for me.
Iphone Hacking with Command
 The iPhone is a multimedia and Internet-enabled quad-band GSM EDGE-supported mobile phone designed and sold by Apple Inc.
The iPhone is a multimedia and Internet-enabled quad-band GSM EDGE-supported mobile phone designed and sold by Apple Inc.The iPhone's functions include those of a camera phone and a multimedia player. It also offers Internet services including e-mail, text messaging, web browsing, Visual Voicemail, and local Wi-Fi connectivity. User input is accomplished via a multi-touch screen with virtual keyboard and buttons. Apple has filed more than 200 patents related to the technology behind the iPhone.
but last info from Hackint0sh.org forum some clever hacker can hack this iPhone with they enable the serial debugging/shell mode on the device. Click here to see what kind command can using it.
Jul 18, 2007
Google keep their cookies at 2 years now
The company said that their cookies will auto delete after two years. This would however happen only if the user does not visit their sites again in this period.
If the user visits the Google website again, the time would reset and it would have a fresh life of two years.
At this moment, the Google cookies are set to delete after 2038.
Peter Fleischer, Google’s global privacy counsel spoke on this new development: “After listening to feedback from our users and from privacy advocates, we’ve concluded that it would be a good thing for privacy to significantly shorten the lifetime of our cookies.”
Cookies are essentially tiny files stored on the user’s computer when he visits a website. This information is later used by the site to remember the stored preferences and other settings.
Jul 17, 2007
Critical security vulnerabilities found in Microsoft's software
Sophos Antivirus vendor has advised computer users to install a number of new critical security patches from Microsoft.
As part of its monthly "Patch Tuesday" schedule Microsoft has issued six new bulletins (three of them labeled "critical") about 11 security vulnerabilities in its software.
Vulnerabilities described in the critical security bulletins include security issues with Microsoft Excel (in both Windows and Apple Mac versions), Windows Active Directory and the .Net Framework. The remaining bulletins address issues in Windows Vista's Firewall, Microsoft Office Publisher 2007 and IIS 5.1 on Windows XP Service Pack 2.
Some of the flaws in Microsoft's code could allow remote code execution, enabling a hacker to access data on a vulnerable PC or run malicious code such as a worm.
Read more about the security patches now, and protect your computers
Graham Cluley, senior technology consultant at Sophos said :
"Businesses and home users must be prepared to regularly install security patches from Microsoft, or risk having vulnerabilities on their PC exploited by hackers."
Microsoft doesn't announce critical security problems in its software for the fun of it - they're warning people of serious issues in the hope that customers will update and protect themselves before hackers can take advantage of the situation. Acting now will help defend your computers and help reduce the risk of cybercriminals running riot.
Home users of Microsoft Windows can visit update.microsoft.com to have their systems scanned for Microsoft security vulnerabilities.
Sophos suggests that every IT manager responsible for security should consider subscribing to vulnerability mailing lists such as that operated by Microsoft at www.microsoft.com/technet/security/bulletin/notify.mspx.
Source : Sophos.com
Microsoft Finishes Windows Home Server
Hewlett-Packard will be the first OEM partner to ship Home Server systems, with Fujitsu-Siemens, Gateway, Iomega, Lacie and Medion also on board. The OS likely won't be available to buy on its own, but a 120-day evaluation version will be posted for download. Microsoft is also encouraging developers to build Windows Home Server add-ins, and has launched a contest to further that effort.
Screenshots :



Macs Affected by Office Flaws
The flaws on Mac have an aggregate security rating of "Important" and involve one calculation error and two memory corruption problems that could lead to a malicious file executing arbitrary code. Users can download Office 2004 for Mac 11.3.6 to plug the security holes. Microsoft notes that version 11.3.5 must be installed first.
Source : Betanews
Windows Media DRM Cracked, Again
The back and forth began last August when a Doom9 forum user by the name of "viodentia" released a program called FairUse4WM. The application was able to strip the copyright protection from both audio and video files, removing restrictions of where and when they could be played. Windows Media files could also then be converted into other formats as well.
Read the Full story here
Jun 30, 2007
Yahoo! Messenger Emoticontest: Expressions to Emoticons
Put on your best face and upload a photo of your favorite expression. Tell your friends to cast their votes and get you into the finals. The winner of the Yahoo! Emoticontest will get their mug made into an emoticon and added to this year’s new Yahoo! Messenger!
Your suggestion needs to be a unique and new idea. Here is a full list of existing emoticons (that you cannot copy). Did you know there were some hidden emoticons and smileys in Yahoo! Messenger too!
Can you think of an emoticon-worthy expression? Then submit it to the emoticon contest and it might just be included in the new version of your favorite IM Yahoo! Messenger someday. People have already submitted many expressions to the contest. Add yours.
Jun 29, 2007
Hairy Harry Potter worm targets USB memory drives
With just weeks remaining until the release of the last ever Harry Potter novel, and the imminent premiere of the fifth movie in the franchise, Sophos has warned of a new computer worm exploiting Potter-mania around the world.
The W32/Hairy-A worm spreads by copying itself onto USB memory sticks, posing as a copy of the eagerly-anticipated novel "Harry Potter and the Deathly Hallows".
Windows users who allow affected flash drives to 'autorun' are automatically infected by the worm when it is attached to their PC. A file called
HarryPotter-TheDeathlyHallows.doc
can be found in the root directory of infected USB drives. Inside the Word document file is the simple phrase "Harry Potter is dead."
Don't download Microsoft Security Bulletin MS07-0065!
Experts at Sophos, a world leader in IT security and control, have warned of a widespread attempt to infect email users by sending them a warning about a bogus Microsoft security patch.
The emails, which have the subject line "Microsoft Security Bulletin MS07-0065" pretend to come from Microsoft, and claim that a zero-day vulnerability has been discovered in the Microsoft Outlook email program. They go on to warn recipients that "more than 100,000 machines" have been exploited via the vulnerability in order to promote medications such as Viagra and Cialis.
Users are encouraged by the email to download a patch which, it is claimed, will fix the problem and prevent them from becoming attacked by hackers.
However, clicking on the link contained inside the email does not take computer users to Microsoft's website but one of many compromised websites hosting a Trojan horse. Sophos proactively detects the Trojan, without requiring an update, using Behavioral Genotype® Protection as Mal/Behav-112.

The emails claim to come from Microsoft.
In examples seen by Sophos experts, the emails have contained the recipient's full name, and the company they work for, in an attempt to lull user's into a false sense of security.
"By using people's real names, the Microsoft logo, and legitimate-sounding wording, the hackers are attempting to fool more people into stepping blindly into their bear-trap," continued Cluley. "Users need to be on their guard against this kind of confidence trick or they risk handing over control of their PC to hackers with criminal intentions. They should also ensure that they are downloading Microsoft security updates from Microsoft itself, not from any other website."
Jun 25, 2007
Suspected mobile phone virus author arrested
Experts at Sophos, a world leader in IT security and control, have welcomed news that Spanish authorities have arrested a man suspected of writing and distributing a mobile phone virus.
According to a statement issued by Spanish police, a 28-year-old man was arrested in Valencia following a seven month investigation. The man is accused of creating and spreading over 20 different variants of the Cabir and Commwarrior worms, which attempt to infect mobile phones running the Symbian operating system. Embedded inside the worms alleged to have been written by the man are references to "Leslie", which is said to be the name of the suspect's fiancee.
Spanish police claim that as many as 115,000 mobile phones may have been struck by the malware.
"Cellphone viruses are not as common as the malware which strikes Windows desktops on a regular basis, but it is just as illegal in its intent. Viruses are not harmless pranks; they cause real harm disrupting business and personal communications as well as destroying and stealing sensitive data," said Graham Cluley, senior technology consultant for Sophos. "The computer crime authorities around the globe are becoming more experienced at tracking down hackers and virus writers, and malware authors should be asking themselves whether it's really worth taking the risk."
In a Sophos survey conducted earlier this year, 81 percent of business IT administrators expressed concern that malware and spyware targeting mobile devices will become a significant threat in the future. However, 64 percent also said they currently have no solution in place to secure company smartphones and PDAs.
Jun 23, 2007
Qooforum new release
This forum have new service call "Ad Revenue Sharing System"
FAQ
Q: Why should I register?A: In order to fully utilize the abilities of this forum, the administrator will probably require that you register as a member. Registration is free, and allows you to do the following:
* Post new threads
* Reply to other peoples' threads
* Edit your posts
* Receive email notification of replies to posts and threads you specify
* Send private messages to other members
* Enter events in the forum calendar
* Set up a 'buddy-list' to quickly see which of your friends are currently online
To register, you will need to specify a username and password, and a valid email address. Entering your email address will not leave you open to 'spam', as you can choose to hide your email address, and messages sent to you via email do not reveal your address to the sender in any case. (To verify this, you can try sending an email message to another user.) The administrator may have configured the forum to send you the final part of the registration process by email, so ensure that the email address you provide is valid and working.
If you are under the age of 13, the administrator may require that a parent or guardian provides consent before allowing you to complete the registration process. More information about this is available during the registration process.
Read more about user maintenance FAQ here
Q: What are referrals?
A: The administrator may have enabled referrals, which allows you to be credited for any new users you invite to the forum.
You gain referrals by promoting QooForum using your unique referral link. The link you should use as your referral link is this:
http://www.qooforum.com/index.php?referrerid=22
Each time someone follows this link to QooForum and registers as a new member, your referral count will be incremented by one. The number of referrals you have can be viewed in your profile.
Your administrator will have more information on any prizes or rewards that may be given out for referrals. Please be courteous when promoting QooForum by not spamming other web sites with your referral link just to gain referrals.
Q: What is "Ad Revenue Sharing System"?
A: It is a system that shares advertisement revenue made by this forum to it's active
members, i.e. you.
Q: What are the requirements to participate?
A: * you must be a registered user and contributed a minimum 50 posts to the forum. Once you have reached that level, your ad code will be applied to all the threads started by you.
* you must have an AdSense Publisher ID, i.e. pub-xxxxxxxxxxxxxxxx. If you do not have an account, you can Sign up for AdSense.
* you must not violate Google AdSense TOS in this forum and any other site with your ad code.
Q: How much can I earn?
A: It depends on your level of participation to the forum. Currently, you are entitled to 50% chance of showing your ad code within the threads that are started by you. Therefore, the more threads you start, the more you will earn.
Q: How do I set it up?
A: Join this forum to find your answer
Sign up Forum
Jun 20, 2007
Windows Live Mail Beta
 Ever use Outlook Express? Windows Live Mail Beta offers similar features, plus some great new ones—like free access to Windows Live Hotmail and integration with other Windows Live services.
Ever use Outlook Express? Windows Live Mail Beta offers similar features, plus some great new ones—like free access to Windows Live Hotmail and integration with other Windows Live services.Fast
* Access multiple e-mail accounts in one place
* Drag, drop, and organize with one click
* Compose and manage e-mail even while you're offline—when you next connect to the Internet, Windows Live Mail will automatically send and receive messages for you
Easy
* Integrated Windows Live services let you launch Messenger right from Mail, and go to Windows Live Spaces with a single click
* Photo E-mail lets you create and send slide shows to friends and family
* All-new, cleaner, easier-to-use interface supports Aero on Vista
* RSS feeds and newsgroup messages are displayed next to your e-mail, and you can search them from within Windows Live Mail
Safer than ever
* Get powerful virus scanning on all of your Hotmail messages
* Enjoy increased protection from phishing scams, across all your e-mail accounts
* Block suspicious messages—and senders, too
* Destroy junk e-mail with a single click
* Color-coded messages help you quickly identify suspicious and safe e-mail
Read FAQ here
System Requirements
Jun 6, 2007
Vulnerabilities strike more AV firms & Mac
Users of Mac OS X, used to a cosy sense of security, have been warned of possible penetration vectors thanks to a slew of flaws unveiled in the Samba networking system used to connect Macs to Windows systems.
An alert issued by Symantec's DeepSight threat team warned Mac users that even if their systems report being fully patched, fixes for the latest batch of vulnerabilities in Samba, reported in early May, are unlikely to be in place, as Apple has apparently not released updates to the system since 2005. While a default installation of Mac OS X includes Samba version 3.0.10, version 3.0.25 is needed to be safe from the latest flaws.
Details of the Samba buffer-overflow issues are here, and patches can be downloaded here.
F-Secure meanwhile joins a growing roster of AV firms rocked by security flaws in their products in recent months, with four separate vulnerabilities in their products reported in the last few days. The most serious is a buffer overflow while scanning LHA archives, which can result in remote system access - a summary from F-Secure is here, and details from
Secunia are here.
Agloco Viewbar Akhirnya Muncul
Screenshoot:
 Tampilan Viewbar bisa dirubah warnanya sesuai dengan keinginan kita , ada 4 warna blue,green,purple dan red sedangkan untuk docking bisa tampilan di TOP desktop atau Bottom Desktop. Versi bahasa yang tersedia saat ini bahasa Inggris dan China. Viewbar yang tersedia dari Agloco saat ini versi Win32.1.00
Tampilan Viewbar bisa dirubah warnanya sesuai dengan keinginan kita , ada 4 warna blue,green,purple dan red sedangkan untuk docking bisa tampilan di TOP desktop atau Bottom Desktop. Versi bahasa yang tersedia saat ini bahasa Inggris dan China. Viewbar yang tersedia dari Agloco saat ini versi Win32.1.00Setelah kita login di kotak isian waktu startup dengan ID dan password kita maka viewbar akan muncul di layar dekstop kita dan di sebelah kanan taskbar ada muncul green cicle yang menandakan viewbar kita mulai aktif.
kita sudah bisa memulai browsing internet , chatting , akses email dan semuanya akan terekam di account kita. jadi ga sabar neh ... kira-kira bisa dapet berapa yah jika sehari dari kantor jam 8 pagi sampe sore jam 6 ? ...Agloco... I love your ways :)
Jun 2, 2007
Makassar, Kota Cyber Pertama RI
Begitu pula pelayanan pemerintah akan dilakukan seluruhnya secara online. Makassar bersiap masuk dalam era dominasi teknologi informasi.
"Mudah-mudahan rencana Makassar Cyber City sudah dapat dilaksanakan tahun 2008 mendatang. Kami mengharapkan dukungan berbagai pihak," ujar Wali Kota Makassar, Ilham Arief Sirajuddin, dalam konferensi pers peresmian Losari Cyber Beach di Hotel Quality, Makassar, Minggu (27/5).
Beberapa provider (penyedia layanan internet) telah menyatakan komitmen untuk mendukung rencana kota internet itu.
Makassar Cyber City adalah menjadikan seluruh wilayah Kota Makassar sebagai area cakupan sinyal internet nirkabel. Istilahnya metropolitan area network (MAN).
Baru-baru ini PT Telkom meluncurkan program Losari Cyber Beach, yaitu hotspot atau area untuk mengakses internet nirkabel di Pantai Losari.
Dengan cakupan sinyal sepanjang 1,2 kilometer, Pantai Losari menjadi area hotspot terbuka pertama dan terpanjang di Indonesia.
Tahun ini, PT Telkom menargetkan pemasangan 300 access point (titik akses internet) di beberapa wilayah di Kota Makassar.
Bersama provider lain, saat ini telah terbangun puluhan hotspot di hotel-hotel berbintang, mal, kampus, dan beberapa instansi swasta.
Yang paling hangat saat ini, para provider sedang bersaing ketat mendapatkan izin pemerintah untuk mengoperasikan teknologi Wi-Max (worldwide interoperability for microwave access). Teknologi ini jauh lebih canggih dari Wi-Fi (wireless fidelity) yang digunakan untuk umumnya hotspot di Indonesia.
"Negara-negara maju telah menggunakan Wi-Max untuk akses internet nirkabel. Kini para provider sedang berebut lisensi untuk itu. Suatu saat nanti, Telkom akan menghadirkannya di Makassar," ujar Executive General Manager PT Telkom Divisi Regional VII, Pahala P Hariandja.
Jika akses internet dengan teknologi Wi-Fi hanya memiliki jangkauan sejauh 100-150 meter dari acces point (pemancar sinyal internet), dengan teknologi Wi-Max nantinya jangkauan akses bisa mencapai 50 kilometer.
Sinyal internet akan dipancarkan melalui sebuah menara semacam BTS untuk ponsel.
Saat teknologi itu hadir, hotspot bukan lagi wilayah-wlayah kecil. Seluruh Kota Makassar akan menjadi area hotspot.
Pengguna laptop, windows mobile, atau smart phone dapat berinternet dari mobil yang melaju di jalan raya, rumah, kantor, kafe, bahkan di tengah sawah di pinggiran Makassar.
Kecepatan transfer data dengan Wi-Max terhitung super cepat. Bila dengan Wi-Fi saja bisa mencapai 11 megabyte per detik, dengan Wi- Max kecepatan transfer bisa mencapai 75 megabyte per detik. Sekitar 1.000-an orang juga dapat mengakses internet dalam satu waktu sekaligus.
Mengenai pelayanan online sudah jamak dilakukan di negara maju. Untuk membuat KTP misalnya, warga cukup mengakses situs kantor kependudukan.
Setelah melakukan verifikasi data, kantor kependudukan memungut biaya dari rekening pemohon melalui perbankan online. KTP pun keluar.
Begitu juga dengan pelayanan peizinan, retribusi, pajak, telepon, listrik, dan sebagainya.
Nantinya, warga dapat membayar tagihan-tagihan cukup melalui internet tanpa harus bertatap muka dengan petugas dan antre panjang di loket pembayaran.
"Memang tidak mudah untuk menyediakan layanan online seperti itu. Butuh dukungan biaya. Untuk pengadaan perangkat lunak (software) dan perangkat keras (hardware) sistem informasi administrasi kependudukan (SIAK) saja, kita menganggarkan sekitar Rp 4 miliar," kata Ilham.
Pelayanan online di Makassar memang baru dapat terlaksana melalui SIAK.
Ini merupakan prestasi yang lumayan. Sebab Kota Makassar adalah satu dari segelintir kota di Indonesia yang telah mengoperasikan sistem online dalam urusan pembuatan KTP.
aktivasi internet nirkabel losari
NOTEBOOK
* Aktifkan fasilitas Wi-Fi dengan mengubah posisi Wi-Fi ke posisi on
* Klik kanan di atas icon wireless network connection (menu task bar) lalu pilih view available wireless network
* Setelah muncul wireless network connection tekan refresh network list
* Akan muncul daftar SSID (access point), pilih Telkom Hotspot Losari lalu tekan connect
* Setelah SSID yang dipilih muncul connected, tutuplah dialog box
* Buka internet browser lalu ketik www.plasa.com
* Akan muncul login page. Masukan user name dan password (untuk masa gratis sampai 30 Juni 2007, Anda dapat menggunakan user name "makassar" dan password "ultah400").
PDA (WINDOWS MOBILE)
* Pilih menu start, -> setting, -> tab connection, -> wireless LAN
* Pilih menu atau icon network cards
* Akan muncul daftar SSID (access point). Pilih dan tekan agak lama salah satu SSID Telkom Hotspot Losari lalu pilih option connect
* Tunggu sampai di SSID yang dipilih muncul connected, lalu tutup dialog box
* Buka internet browser lalu ketik www.plasa.com
* Akan muncul login page. Masukan user name dan password (untuk masa gratis sampai 30 Juni 2007, Anda dapat menggunakan user name "makassar" dan password "ultah400").
SMARTPHONE (NOKIA 9500 ATAU 9300I)
* Pilih tools -> control panel -> connection -> wireless internet
* Akan muncul daftar SSID (access point). Pilih salah satu SSID Telkom Hotspot Losari
* Tekan tombol create access point dan pilih done
* Tekan tombol "web" -> GOTO (tombol kanan atas)
- Ketik www.plasa.com
- Akan muncul daftar SSID. Pilih nama SSID yang telah di-create tadi
- Akan muncul login page. Masukan user name dan password (untuk masa gratis sampai 30 Juni 2007, Anda dapat menggunakan user name "makassar" dan password "ultah400").
(jid)
Sumber :tribun-timur.com
May 26, 2007
Outlook Duplicate Items Remover
Using ODIR is very easy: select a folder and click the button Remove Duplicate Items. ODIR scans the selected folder for duplicates and MOVES all duplicates found to a subfolder ODIR_duplicate items. ODIR recognizes an item as a duplicate if all of the following properties match those of another item in the same folder :
- Contact items : first name, last name, company name and email address
- Appointment items : subject, location, start date and end date
- Task items : subject, start date, due date and status
- Note items : contents of the note (Body property) and color
- E-mail or Post items :
- received emails : the internet message ID (this is a unique identifier for each email received)
- sent emails : email subject and the time the email is sent
- unsent emails: email subject only
Publisher : Visit Website
DOWNLOAD NOW (1916 KB)
Protect Files with DCCExplorer

Features:
- No installation needed, run on any computer on Windows 98/Me/2k/XP.
- Encrypt any files and folders fast.
- No need to re-enter password when encrypt (use last password or default password)
- Support file masks to encrypt. Encrypt (include) or not encrypt (exclude) only files that match the file masks you want. You can adjust file masks to each folder.
- Compress your files with 9 levels when encrypt (zip level).
- Save your encryption setting of each file or folder for the next encryptions.
- Prevent using file recovery software to recover your un-encrypted files which was deleted by the software.
- Drag and Drop.
- Open and save the list of your files which need to be protected.
DOWNLOAD NOW (242 KB)
Portable Antivirus

Features:
- Scan all your hard drive in one push of button
- Scan your system process
- Scan your PC by selected path
- Giving you an choice of scanning
- Clearing your temporary folder and recycled bin during scan
- Free updates
- Automatically fix all modified registry causes by malware
Publisher : Visit Website
DOWNLOAD NOW (194 KB)May 24, 2007
Gadget For Windows Vista


Vista make slowly computer ?
Tips for Slowly computer running in Vista :
- Check the computer configuration against recommended requirements for Windows® Vista™.
Minimum system requirements for Windows Vista :
* 800 MHz 32-bit (x86) or 64-bit (x64) processor
* 512 MB memory
* 800 x 600 SVGA display
* 20 GB hard drive space, including 15 GB available free space
Recommended system requirements for Windows Vista :
* 1.0 GHz or faster x86 or x64 processor (single or multiple core)
* 1 GB memory
* Windows Aero capable graphics requires DirectX 9-class GPU that supports a WDDM
driver, Pixel Shader 2.0 in hardware, and 32 bits per pixel.
* Adequate graphics memory
* 40 GB hard drive space, including 15 GB available free space - Run Windows Update:
1. Click Start. In the Start Search box, type: Windows. From the displayed list, select Windows Update.
2. Verify "Windows is up to date" with important updates.
3. If not, install updates. - Run Anti-spyware Scan (Windows Defender):
1. Click Start. In the Start Search box, type: Windows. From the displayed list, select Windows Defender.
2. On the toolbar, click Scan.
3. System scans for spyware.
4. After scan has finished and if items are found, remove items from Quarantined items. - Run Antivirus Scan
1. Open Antivirus program, and then click on Scan.
2. System scans for viruses.
3. After scan has finished and if items are found, remove items from Quarantined items.
- Clear Browsing History.
Open the properties for Internet Explorer 7 using one of the following methods:
** Click Start, right-click Internet, and then click Internet Properties.
** Click Start. At the top of the list, click on Internet, then click Tools, and then click Internet Options.
** Click Start, in the Start Search box, type: Options. From the displayed list, select Internet Options.
To delete all browsing history:
1. Under Browsing History, click Delete.
2. Click Delete all.
3. At the Delete Browsing History pop-up, check Also delete files.
4. Click Yes.
To delete Temporary Internet Files via the Folders route:
1. Under Browsing History, select Settings.
2. Click View Files.
3. Select all files (Press CTRL+A).
4. Press the Delete Key.
5. At the Warning confirmation screen, click Yes.
6. Files are deleted.
7. Click OK to return to Internet Options.
Note: If there are multiple User Names, repeat the Delete Temporary Internet Files process for each user name. - Use Disk cleanup to remove additional files on drive:
1. Click Start, in the Start Search box, type Disk. From the displayed list, select Disk Cleanup.
2. At the prompt, select either My files only or Files from all users on this computer.
3. On the UAC prompt, click continue.
4. Select drive to clean (usually C:).
5. Check files to be deleted (description below will explain deletions.)
6. Click OK at prompt, and then click Delete Files.
7. Disk cleanup starts and cleans. - Remove unwanted programs:
1. Click Start. In the Start Search box, type: Programs. From the displayed list, select Programs and Features.
2. Remove the unwanted programs. - Use Check Disk (chkdsk) to repair your hard drive:
1. Click Start. In the Start Search box, type: cmd. From the displayed list, right-click cmd, and then select Run as administrator.
2. On the UAC prompt, click continue.
3. At prompt, type: chkdsk c: /r.
4. A message that the drive is locked appears. Type Y to run at next restart.
5. At the prompt, type: exit.
6. Restart system. - Run Disk Defragmenter to defragment the hard drive:
1. Click Start. In the Start Search box, type: Disk. From the displayed list, select Disk Defragmenter.
2. Once open, click Defragment now. - Adjust Windows Appearance to disable the fancy "Visually Pleasant" features of Vista:
1. Right-click anywhere on the desktop. From the menu, select Personalize.
2. Select Windows Color and Appearance.
3. Select Open Classic Appearance properties for more color options.
4. Select Windows Vista Basic or Windows Standard, and then click OK.
5. Test to see if the system is running faster.
* Run programs that were previously regarded as running slow.
* Access the internet and view frequently visited sites. - Utilize "Performance Information and Tools" task.
** Click Start. In the Start Search box, type: Per. From the displayed list, select Performance Information and Tools.
** Adjust Visual Effects:
1. Select Adjust Visual Effects. On the UAC prompt, click continue.
2. Change this to Adjust for best performance (This removes all checks from boxes), and then click OK.
3. This sets your color scheme to Windows Standard and no added features.
4. Test to see if the system is running faster. Run programs that were previously regarded as running slow. Access the internet and view frequently visited sites.
** Adjust Power Settings:
1. Select Adjust Power Settings. Click continue on UAC prompt
2. Change this to High performance. Click back arrow at top left of screen to go back to previous screen
3. Test to see if the system is running faster.
* Run programs that were previously regarded as running slow.
* Access the internet and view frequently visited sites.
** Performance issues reported:
1. Select Advanced tools.
2. Check for Performance issues under the heading "Performance issues".
3. Make any modifications that are suggested.
4. Test to see if the system is running faster.
* Run programs that were previously regarded as running slow.
* Access the internet and view frequently visited sites.
** Cleanup Desktop Icons and Quick Launch applications:
1. On the desktop, right-click on any unused icon and then click Delete.
2. In Quick Launch, right-click any unused icon and then click Delete.
** You can improve your computer's performance by preventing unnecessary programs from running automatically when Windows starts:
1. Click Start. In the Start Search box, type: SYS. From the displayed list, select System Configuration.
2. On the UAC prompt, click continue.
3. Once open, click on the Services tab, and then place a check in Hide all Microsoft Services. Click Disable All.
4. Click the Startup tab. Click Disable All.
5. Click OK. When prompted, restart the computer.
6. Test to see if the system is running faster.
* Run programs that were previously regarded as running slow.
* Access the internet and view frequently visited sites.
Note:If the system is performing better, start adding back disabled services one at a time. Verify system performance after each addition. - If updated drivers are available, install the updated drivers.
1. Click Start. In the Start Search box, type: dev. From the displayed list, select Device Manager.
2. On the UAC prompt, click Continue.
3. Select a device and click the plus sign (+) to open the device.
4. Right-click on the device and select Update Driver Software....









